Microsoft Cybersecurity Architect SC-100 Exam Questions
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling adaptive network hardening.
Does this meet the goal?
Answer : B
A customer has a Microsoft 365 E5 subscription and an Azure subscription.
The customer wants to centrally manage security incidents, analyze log, audit activity, and search for potential threats across all deployed services.
You need to recommend a solution for the customer. The solution must minimize costs.
What should you include in the recommendation?
Answer : D
Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit.
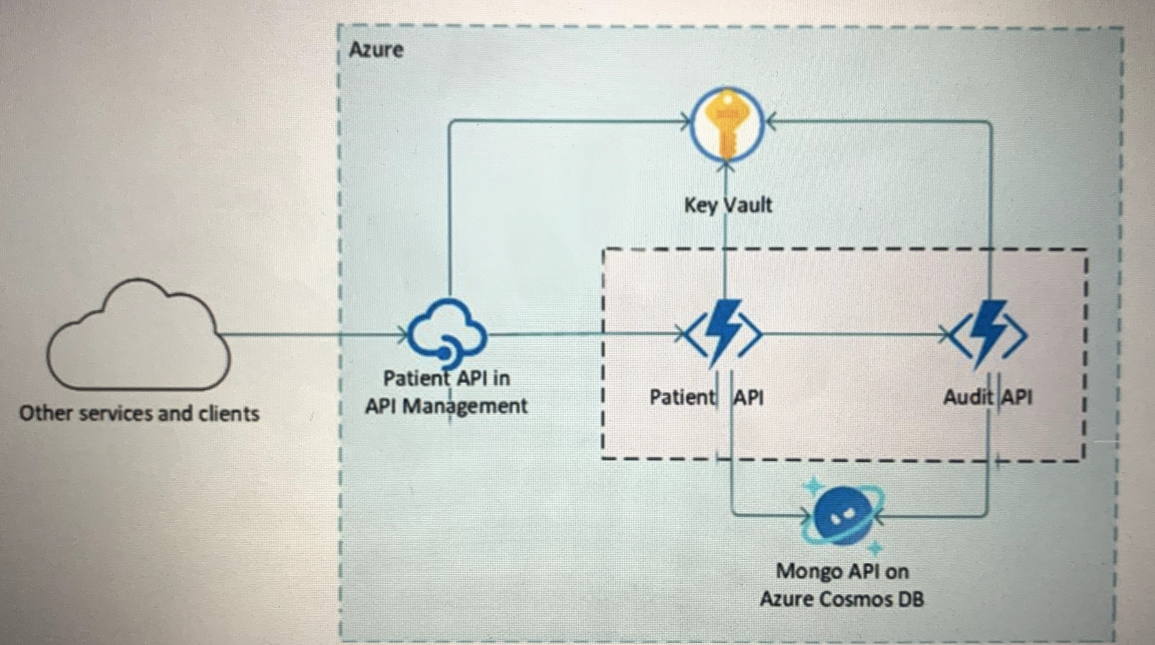
You need to recommend a solution to isolate the compute components on an Azure virtual network. What should you include in the recommendation?
Answer : B
App Service environments (ASEs) are appropriate for application workloads that require:
Very high scale,Isolation and secure network access,High memory utilization.This capability can host your:
Windows web apps,Linux web apps
Docker containers,Mobile apps
Functions
https://docs.microsoft.com/en-us/azure/app-service/environment/overview
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
You have an Azure AD tenant that syncs with an Active Directory Domain Services (AD DS) domain.
You are designing an Azure DevOps solution to deploy applications to an Azure subscription by using continuous integration and continuous deployment (CI/CD) pipelines.
You need to recommend which types of identities to use for the deployment credentials of the service connection. The solution must follow DevSecOps best practices from the Microsoft Cloud Adoption Framework for Azure.
What should you recommend?
Answer : A
You have a Microsoft Entra tenant named contoso.com.
You have an external partner that has a Microsoft Entra tenant named fabrikam.com.
You need to recommend an identity governance solution for contoso.com that meets the following requirements:
Enables the users in contoso.com and fabrikam.com to communicate by using shared Microsoft Teams channels.
Manages access to shared Teams channels in contoso.com by using groups in fabrikam.com.
Supports single sign-on (SSO).
Minimizes administrative effort.
Maximizes security.
What should you include in the recommendation?
Answer : D
You have a Microsoft Entra tenant. The tenant contains 500 Windows devices that have the Global Secure Access client deployed.
You have a third-party software as a service (SaaS) app named App1.
You plan to implement Global Secure Access to manage access to App1.
You need to recommend a solution to manage connections to App1. The solution must ensure that users authenticate by using their Microsoft Entra credentials before they can connect to App1.
What should you include the recommendation?
Answer : A