Netskope Certified Cloud Security Administrator Exam NSK101 NCCSA Exam Practice Test
Click the Exhibit button.
Referring to the exhibit, which statement accurately describes the difference between Source IP (Egress) and Source IP (User) address?
Click the Exhibit button.
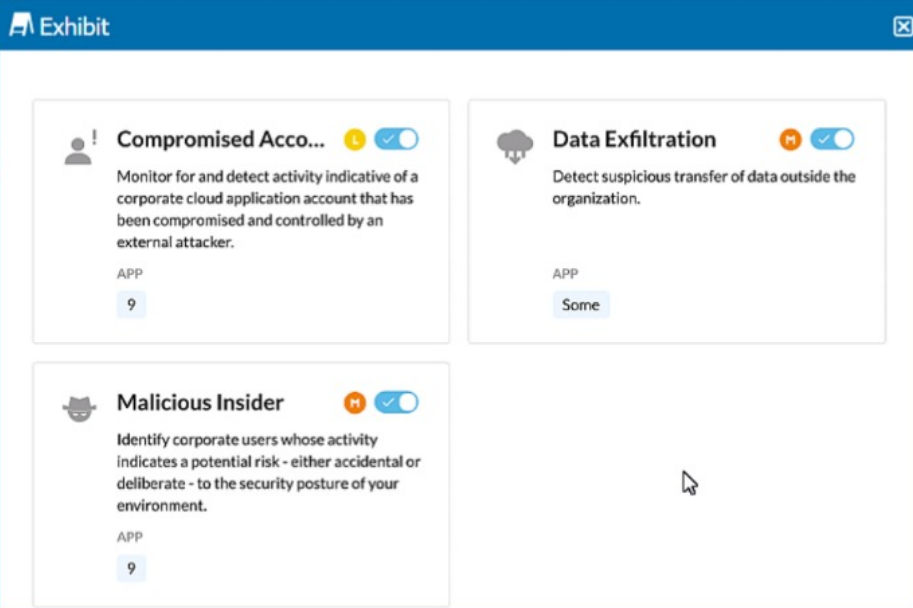
The exhibit shows security rules that are part of which component of the Netskope platform?
Answer : D
The exhibit displays rules related to detecting compromised accounts, data exfiltration, and malicious insiders. These types of activities are typically analyzed and detected through user behavior analytics, which involves monitoring and analyzing the behavior of users to identify anomalies that may indicate security incidents or threats.
Behavior Analytics is a component of the Netskope platform that focuses on identifying potential security risks based on user behavior. This includes monitoring for compromised accounts, data exfiltration, and identifying malicious insiders. These analytics help in proactively identifying and mitigating threats by analyzing patterns and anomalies in user activities.
The exhibit showing rules related to compromised accounts, data exfiltration, and malicious insiders aligns with the capabilities provided by Behavior Analytics.
Documentation from the Netskope Knowledge Portal on the behavior analytics capabilities supports this identification.
The Netskope deployment for your organization is deployed in CASB-only mode. You want to view dropbox.com traffic but do not see it when using SkopeIT.
In this scenario, what are two reasons for this problem? (Choose two.)
Answer : A, B
In a CASB-only deployment of Netskope, there could be several reasons why Dropbox.com traffic is not visible in SkopeIT:
Certificate Pinning:
The Dropbox Web application might be using certificate pinning, which means it only accepts specific certificates for its connections. This can prevent the traffic from being steered to the Netskope tenant because the proxy's certificate might not match the pinned certificate.
Configuration of Dropbox Domains:
If the Dropbox domains are not properly configured to be steered to the Netskope tenant, then the traffic will bypass the Netskope inspection and will not be visible in SkopeIT. Ensuring that the domains are configured correctly is essential for the traffic to be captured and analyzed by Netskope.
'Certificate pinning prevents the interception of traffic by requiring that the presented certificate matches a known good certificate. This can interfere with traffic steering in CASB deployments.'.
'Proper configuration of application domains is necessary to ensure traffic is steered to the Netskope tenant for inspection and visibility.'.
Click the Exhibit button.
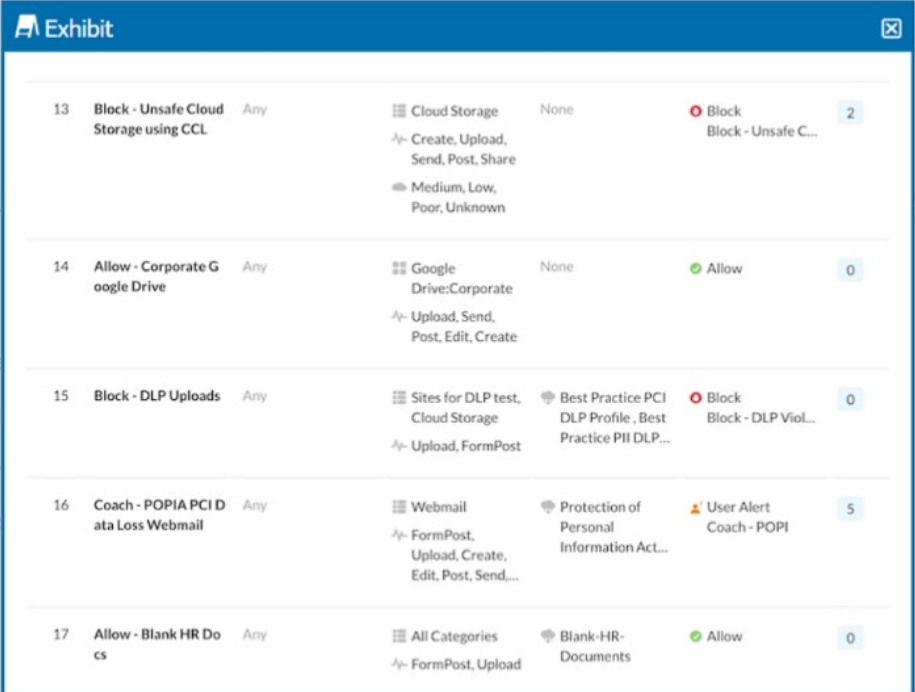
A user is uploading a file containing PCI-DSS data to the corporate Google Drive instance. You notice that the upload is not blocked by the policy shown in the exhibit. Which statement is correct in this scenario?
Answer : C
In the exhibit, a user is uploading a file containing PCI-DSS data to the corporate Google Drive instance. Despite the policy that blocks DLP (Data Loss Prevention) uploads being active, the upload is not blocked. This indicates that the policy is not applied in the correct order.
Netskope applies policies in a top-down manner. If there are multiple policies that could apply to an action, the order in which the policies are evaluated is crucial. In this case, another policy might be allowing the upload before the DLP policy can block it. Ensuring that the DLP policy is higher in the order can resolve this issue.
Netskope policy configuration and enforcement documentation.
Details on how Netskope processes and applies policies based on their order in the policy list.
A customer wants to detect misconfigurations in their AWS cloud instances.
In this scenario, which Netskope feature would you recommend to the customer?