Netskope Certified Cloud Security Architect NSK300 Exam Practice Test
Review the exhibit.
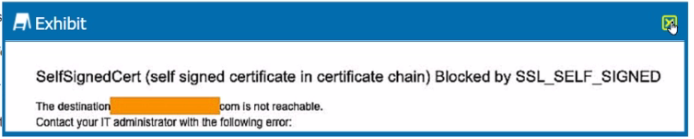
You are the proxy administrator for a medical devices company. You recently changed a pilot group of users from cloud app steering to all Web traffic. Pilot group users have started to report that they receive the error shown in the exhibit when attempting to access the company intranet site that is publicly available. During troubleshooting, you realize that this site uses your company's internal certificate authority for SSL certificates.
Which three statements describe ways to solve this issue? (Choose three.)
Answer : A, B, D
A . Import the root certificate for your internal certificate authority into Netskope:
This step ensures that Netskope recognizes and trusts SSL certificates issued by your company's internal certificate authority. By importing the root certificate, you enable proper SSL inspection and validation for internal sites.
B . Bypass SSL inspection for the affected site(s):
Since the intranet site uses your company's internal certificate authority, bypassing SSL inspection for this specific site allows users to access it without encountering SSL errors.
D . Change the SSL Error Settings from Block to Bypass in the Netskope tenant:
Adjusting the SSL Error Settings to ''Bypass'' allows users to proceed past SSL errors, including self-signed certificate errors. This ensures uninterrupted access to the intranet site.Reference:
Netskope Security Cloud Introductory Online Technical Training
Netskope Security Cloud Operation & Administration (NSCO&A) - Classroom Training
Netskope Cloud Security Certification Program
Review the exhibit.
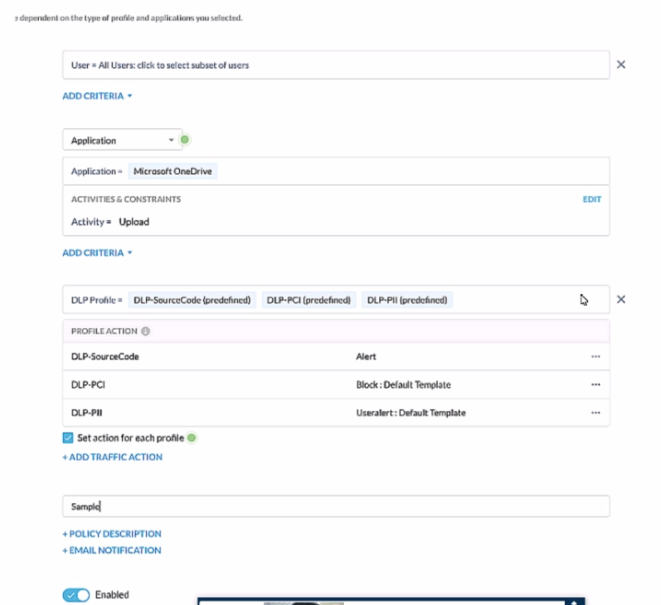
A user has attempted to upload a file to Microsoft OneDrive that contains source code with Pll and PCI data.
Referring to the exhibit, which statement Is correct?
Answer : C
In the given scenario, a user is attempting to upload a file containing sensitive PII and PCI data to Microsoft OneDrive. The Netskope Security Cloud provides real-time data and threat protection when accessing cloud services, websites, and private apps from anywhere, on any device. Based on the exhibit provided, different DLP (Data Loss Prevention) profiles are triggered - DLP-SourceCode, DLP-PCI, and DLP-PII. Each of these profiles has specific actions associated with them; for instance, an alert is generated for Source Code while blocking actions are initiated for PCI and PII data. Since multiple DLP profiles are triggered due to the sensitive nature of the content in the file being uploaded, separate incidents will be generated for each matching profile ensuring comprehensive security coverage and incident reporting.
You want to integrate with a third-party DLP engine that requires ICAP. In this scenario, which Netskope platform component must be configured?
Answer : D
When integrating a third-party Data Loss Prevention (DLP) engine that requires ICAP, the Netskope platform component that must be configured is theNetskope Adapter. The Netskope Adapter is designed to facilitate the integration of Netskope with various third-party tools and services, including DLP engines that use ICAP for communication. By configuring the Netskope Adapter, you can ensure that the third-party DLP engine can communicate effectively with the Netskope platform to provide comprehensive data protection.
Your organization's software deployment team did the initial install of the Netskope Client with SCCM. As the Netskope administrator, you will be responsible for all up-to-date upgrades of the client.
Which two actions would be required to accomplish this task9 (Choose two.)
Answer : A, C
To ensure that the Netskope Client is always up-to-date with the latest upgrades, two actions are required. First, in the Client Configuration, the administrator should set the option toUpgrade Client Automatically to Latest Release. This setting ensures that the client will automatically update to the most recent version available. Second, during the original installation of the Netskope Client, theautoupdate-onflag should be set. This flag enables the auto-update feature, allowing the client to receive and apply updates as they are released.
You are deploying the Netskope Client to Windows devices. The following command line would be used to install the client MSI file:

In this scenario, what is
Answer : B
In the context of deploying the Netskope Client to Windows devices, <token> in the command line refers to the Netskope organization ID. This is a unique identifier associated with your organization's account within the Netskope security cloud. It is used during the installation process to ensure that client devices are registered and managed under the correct organizational account, enabling appropriate security policies and configurations to be applied.Reference: The answer can be inferred from general knowledge about installing software clients and isn't directly available on Netskope's official resources.
You are the network architect for a company using Netskope Private Access. Multiple users are reporting that they are unable to access an application using Netskope Private Access that was working previously. You have verified that the Real-time Protection policy allows access to the application, private applications are steered for the users, and the application is reachable from internal machines. You must verify that the application is reachable through Netskope Publisher
In this scenario, which two tools in the Netskope Ul would you use to accomplish this task? (Choose two.)
Answer : A, B
In the scenario where users are unable to access an application through Netskope Private Access, and after verifying that the Real-time Protection policy allows access, the application is steered for the users, and it is reachable from internal machines, the next step is to verify the application's reachability through the Netskope Publisher. The two tools in the Netskope UI that would be used to accomplish this task are:
A .Reachability Via Publisherin the App Definitions page - This tool allows you to check if the application is reachable through the configured Publishers. It is essential to ensure that the application's connectivity is intact and that there are no issues with the Publishers themselves.
B .Troubleshooter toolin the App Definitions page - The Troubleshooter tool can help diagnose and resolve issues related to application reachability. It provides insights into potential problems and offers guidance on how to fix them.
These tools are designed to assist in troubleshooting and ensuring that applications are accessible through Netskope Private Access.
Review the exhibit.
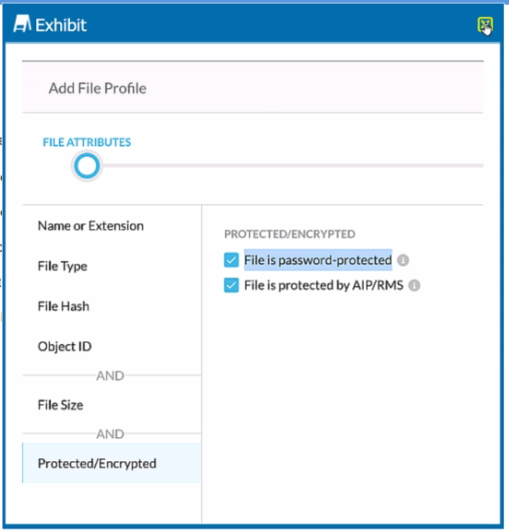
You are attempting to block uploads of password-protected files. You have created the file profile shown in the exhibit.
Where should you add this profile to use in a Real-time Protection policy?
Answer : A
In Netskope Cloud Security, to block uploads of password-protected files, you should add the file profile to a DLP (Data Loss Prevention) profile that is used in a Real-time Protection policy. The DLP profiles in Netskope are designed to detect and protect sensitive data in real-time and at rest across the cloud environment. This approach ensures that any file matching the criteria set in the file profile, such as being password-protected, will trigger the DLP rules and prevent the upload action in real-time.