Nutanix Certified Professional - Cloud Integration - AWS v6.7 NCP-CI-AWS Exam Practice Test
An administrator has been tasked with ensuring NC2 VMs are able to access AWS resources. The NC2 VM traffic must not traverse the internet.
in which two ways would the administrator achieve this? (Choose two.)
Answer : C, D
To ensure that NC2 VMs can access AWS resources without traversing the internet, the administrator can use AWS VPC Peering and Interface Endpoints. Both methods ensure that traffic stays within the AWS network, maintaining security and efficiency.
Interface Endpoint:
Interface Endpoints allow you to privately connect your VPC to supported AWS services. They use AWS PrivateLink to route traffic directly to services within the AWS network, bypassing the public internet.
Steps:
Create an interface endpoint for the required service in the AWS VPC console.
Ensure the security groups and route tables are configured to allow traffic to the interface endpoint.
VPC Peering:
VPC Peering allows the routing of traffic between VPCs using private IP addresses, without the need for internet gateways, NAT devices, or VPN connections.
Steps:
Create a VPC peering connection between the VPCs.
Update the route tables to direct traffic between the peered VPCs.
Ensure security group rules allow the necessary traffic between VPCs.
AWS Interface Endpoint Documentation
Nutanix Cloud Clusters on AWS Administration Guide
Exhibit.

What action is taken against the Condemned node shown in the exhibit?
Answer : A
When a node is marked as 'Condemned,' it indicates that the system has determined that the node is no longer reliable for operations. As part of the automated recovery and protection process, the following action is typically taken:
The node has a power reset sent to it (Answer A):
In most cases, a condemned node undergoes a power reset as an initial recovery attempt. This action attempts to reboot the node to bring it back to a healthy state. If the reset fails, further manual or automated steps may be required to address the hardware or software issue.
Nutanix Cluster Management Documentation
Nutanix Support Knowledge Base
An administrator has been tasked with deploying a new production NC2 cluster on AWS and is studying the deployment..
AWS supports EC2 bare-metal instances in regions with at least how many partitions?
Answer : B
AWS supports EC2 bare-metal instances in regions with at least 3 partitions. Partitions in AWS provide high availability and fault tolerance by distributing instances across different hardware to minimize the impact of hardware failures.
During the recovery of entities protected by Cluster Project, an administrator discovers that the recovery plan is not executing correctly because it exceeds the number of supported entities.
How many entities can be recovered using a Single recovery plan?
Answer : C
The Nutanix disaster recovery capabilities include recovery plans that define how entities are recovered in the event of a failure. There is a limit to the number of entities that can be managed within a single recovery plan.
Entity Limit:
According to Nutanix documentation, the maximum number of entities that can be recovered using a single recovery plan is 300. Exceeding this limit will cause issues during the execution of the recovery plan.
Impact of Exceeding the Limit:
If the number of entities in a recovery plan exceeds the supported limit, the recovery process may fail or not execute correctly, as observed in the scenario.
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Disaster Recovery Best Practices Documentation
An administrator is tasked with providing VMs outbound internet connectivity in AWS.
Which components would the administrator need to create in the VPC to achieve this?
Answer : B
To provide VMs with outbound internet connectivity in AWS using a private subnet, the administrator needs to create the following components in the VPC:
Private Subnet: A private subnet is required to house the VMs that need outbound internet access but do not require direct inbound access from the internet.
NAT Gateway: A NAT (Network Address Translation) Gateway is necessary to allow instances in the private subnet to connect to the internet or other AWS services while preventing the internet from initiating a connection with those instances.
Public EIP (Elastic IP Address): An EIP is associated with the NAT Gateway to provide a persistent public IP address that allows outbound internet traffic from the private subnet to be routed correctly.
Route Table: A route table is configured to route traffic from the private subnet to the NAT Gateway for outbound internet access.
Which NC2 user role will allow full access to clusters created within an organization?
Answer : B
In Nutanix Cloud Integration with AWS, specifically version 6.7, the role that allows full access to clusters created within an organization is the Organization Administrator.
The Organization Administrator role has the highest level of privileges within an organization, enabling the user to manage all aspects of the clusters, including creation, modification, and deletion.
This role is designed to oversee and control the entire organization's resources, ensuring comprehensive management capabilities over all clusters and associated resources.
Reference: Refer to the Nutanix documentation on roles and permissions for NC2 on AWS for further details.
An administrator has deployed an NC2 on AWS cluster that is running mixed workloads. Multiple SQL database are running on the NC2 cluster using a native subnet of 10.78.1.0/24.
The administrator wants to ensure only application servers from source subnet 10.79.1.0/24 that reside outside of the NC2 cluster can access the databases.
Which two actions will help the administrator most securely achieve this? (Choose two.)
A)
B)

C)

D)
Answer : A, D
To ensure that only application servers from the source subnet 10.79.1.0/24 can access the SQL databases running on the NC2 cluster in the subnet 10.78.1.0/24, the administrator can take the following actions:
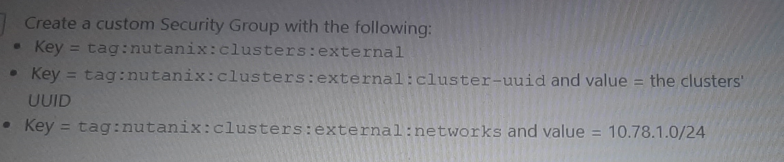
Option A: Create a custom Security Group with the following rules:
Key = tag:nutanix:clusters
Key = tag:nutanix:clusters:external
and value = the clusters' UUID
Key = tag:nutanix:clusters:external
and value = 10.78.1.0/24
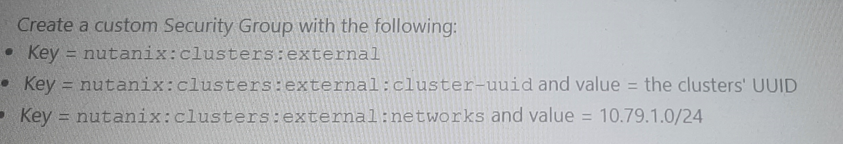
Option D: Create a custom Security Group with the following:
Key = nutanix:clusters
Key = nutanix:clusters:external
and value = the clusters' UUID
Key = nutanix:clusters:external
and value = 10.79.1.0/24
These actions help create security rules that restrict access to the databases only from the specified source subnet, ensuring secure and controlled access.