Nutanix Certified Professional - Unified Storage v6.10 NCP-US Exam Practice Test
[Configure and Utilize Nutanix Unified Storage]
What would an administrator need to do in order to move tagged objects to a remote Nutanix Objects instance after a period of time?
Answer : A
[Troubleshoot Nutanix Unified Storage]
A Nutanix Files cluster isunreachableafter an administrator changed itsname.
What should the administrator do to solve the problem?
Answer : B
[Configure and Utilize Nutanix Unified Storage]
What is a requirement for Smart DR?
Answer : C
[Configure and Utilize Nutanix Unified Storage]
An administrator needs to move infrequently accessed data to lower-cost storage based on file type and owner, and automatically recall data if data access frequency has increased.
What should administrator do to satisfy these requirements?
Answer : D
[Configure and Utilize Nutanix Unified Storage]
What is the maximum number of snapshots that can be configured for a Nutanix Files snapshot schedule?
Answer : D
[Deploy and Upgrade Nutanix Unified Storage]
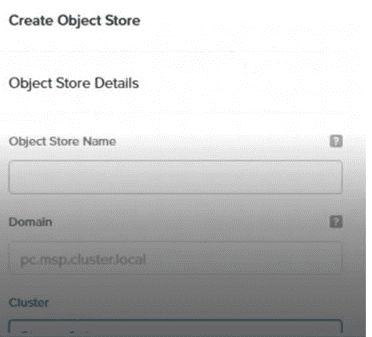
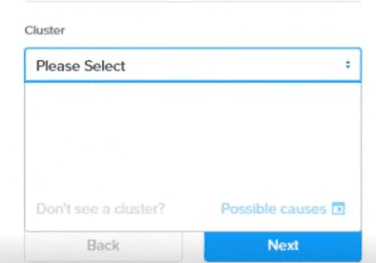
A user is logged into Prism Central and has been tasked with creating a new object store.
What could be the cause no clusters are being listed?
Answer : D
[Deploy and Upgrade Nutanix Unified Storage]
A company is planning to upgrade the Nutanix Objects cluster deployed on-premise to the latest version. An administrator has logged into Prism Central using domain credentials. After navigating to the LCM page and performing an inventory, the administrator notices that the latest version of Objects is not showing. The following components have been updated to the latest available version listed in LCM: MSP Controller, Objects Manager, Objects Services. After running an LCM inventory successfully, the latest version of Objects still is not listed. What could be the reason?
Answer : C