Nutanix Certified Services Core Infrastructure Professional v6.8 NCS-Core Exam Practice Test
Refer to the exhibit.
An administrator logged into Prism Element, notices the following in the home dashboard, and showing the exhibit.
Which action should the administrator take next?
Answer : A
The exhibit shows a screenshot of a Prism Element home dashboard with a notification that ''Data Resiliency not possible'' and warnings about the inability to get configured fully qualified domain names (fqdn) for hosts identified by their node numbers.
Refer to Exhibit:
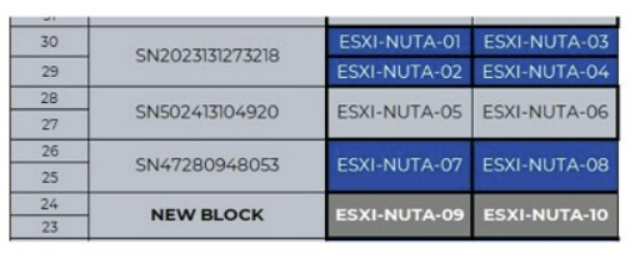
A customer is preparing to expand a cluster with a consultant. The production cluster is comprised of one NX-3460-G7 and two NX-8235 G8 blocks. The running AOS version is 5.20.4.6 and Hypervisor version is ESXi 6.7 U3b. vCenter is also running a 6.7 version.
One NX-3235-G9 block will be added to that cluster (ESXI-NUTA-09 and ESXI-NUTA-10).
The consultant has verified Nutanix documentation and customer's As-Built guide:
* NX-3060-G7 and NX-8035-G8 are hybrid HCI nodes
* ESXi 6.7 U3b is unsupported for the new G9 hardware model
* AOS 5.20.X and ESXi 6 X are end of support
* NX-3060-G7 and NX-8035-G8 hypervisors can be upgraded to the latest ESXi supported version
What actions should be taken before beginning the cluster expansion?
Answer : A
Before expanding the cluster with the new NX-3235-G9 block, it is critical to ensure that all components are running supported and recommended versions due to compatibility and support issues. Therefore, the necessary actions include: A. Upgrade vCenter, AOS, and ESXi to supported and recommended versions. This step ensures compatibility across all components, particularly important as the new G9 hardware does not support the currently installed version of ESXi. Upgrading these components will also ensure continued vendor support and the stability of the environment. Options B, C, and D do not adequately address the need for vCenter upgrades or the fact that ESXi 6.7 U3b is unsupported for G9, highlighting the necessity for a comprehensive upgrade. Reference: Nutanix Hardware Compatibility List, Nutanix Support Portal.
A consultant has deployed a Nutanix cluster with AOS 5.10.x, then discovers the customer's environment is running on AOS 5.6.x. The consultant decides to re-image the cluster using the foundation Java applet. During the Foundation discovery, all cluster nodes display a status of Unavailable.
What should the consultant do to resolve the issue?
Answer : A
When a Nutanix cluster needs to be re-imaged and nodes are showing as 'Unavailable' during the discovery process in the Foundation tool, it is often due to a deeper issue with the nodes' existing configuration or software state. Using the Phoenix ISO to re-image the nodes is the recommended approach. The Phoenix ISO can be used to completely reinstall the software on the nodes, ensuring that any problematic configurations or software issues are wiped clean, allowing for a fresh installation with the desired version of AOS.
An administrator is deploying a new application to a Nutanix Enterprise Cloud. The application requires a security to prevent unauthorized access. The application also uses many non-standard ports that are unique to it. Security should not be changed for existing applications.
What should the administrator do to meet these requirement?
Answer : C
To ensure the new application is securely deployed without affecting existing applications, the administrator should create new categories for the VMs hosting the new application. This approach allows for targeted application of security policies without impacting other applications. After creating these new categories, the administrator should then create new security policies that incorporate these categories and specify the unique, non-standard ports used by the application, ensuring that security is tailored specifically to the new application's needs. Reference: Nutanix Prism Central Guide, Nutanix Security Configuration Best Practices.
Which two components must be identified to validate that software compatibility requirements are met for Nutanix Cluster Installation? (Choose two.)
Answer : B, D
Validating software compatibility for a Nutanix cluster installation necessitates the identification of the AOS version and the type of Hypervisor in use. AOS is central to the Nutanix infrastructure, governing storage, compute, and networking functions. The hypervisor layer is critical as it supports the virtual machines running on the cluster. Compatibility between these components ensures stable operation and support for all features. Reference: Nutanix Certified Services - Core (NCS-Core) Learning Documents
An administrator manages the following two Nutanix AOS 5.15 cluster environment:
* Corp-cluster-01
* Corp-cluster-02
The VM images must be available only on Corp-cluster-01, but cannot be checked out to cluster Corp-cluster-02. The images also cannot be checked out to any other clusters that are registered with Prism Central in the future.
Which two configuration settings must the administrator choose when creating the image placement policy that satisfies the stated requirements? (Choose two.)
A consultant is using a customer's switch for installation. Although the 10GbE ports for each of the hosts are connected to the switch, the nodes fail to be discovered.
What is causing the issue?
Answer : A
The failure to discover nodes during installation can often be attributed to the lack of IPv6 support on the network, especially if the Foundation process relies on IPv6 for node discovery. If IPv6 is not enabled on the customer's switch, the discovery packets may not be properly routed, resulting in the nodes not being discovered. Enabling IPv6 on the switch could resolve this discovery issue.
Nutanix Foundation Troubleshooting Guide: Nutanix Support Portal
Network Configuration and Troubleshooting Documentation