Palo Alto Networks Certified Network Security Administrator PCNSA Exam Practice Test
Based on the graphic, what is the purpose of the SSL/TLS Service profile configuration option?
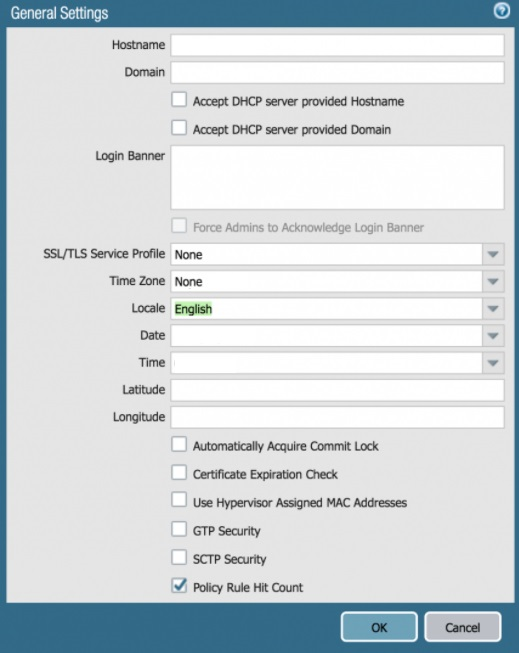
Answer : C
Which statements is true regarding a Heatmap report?
Answer : B
Which object would an administrator create to block access to all high-risk applications?
Answer : B
Explanation/Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClKECA0
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
Answer : A
GlobalProtect: GlobalProtect safeguards your mobile workforce by inspecting all traffic using your next-generation firewalls deployed as internet gateways, whether at the perimeter, in the Demilitarized Zone (DMZ), or in the cloud.
Which statement is true about Panorama managed devices?
Answer : D
Explanation
Explanation/Reference:
What must be configured before setting up Credential Phishing Prevention?
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
Answer : B