Palo Alto Networks Security Service Edge Engineer SSE-Engineer Exam Practice Test
Where are tags applied to control access to Generative AI when implementing AI Access Security?
Answer : A
When implementing AI Access Security, tags are applied to Generative AI applications to classify them as sanctioned, tolerated, or unsanctioned. This allows organizations to enforce policy-based access control over AI tools, ensuring that only approved applications are accessible while restricting or monitoring usage of untrusted or high-risk AI platforms. This classification helps security teams manage AI-related risks and compliance effectively.
Based on the image below, which two statements describe the reason and action required to resolve the errors? (Choose two.)
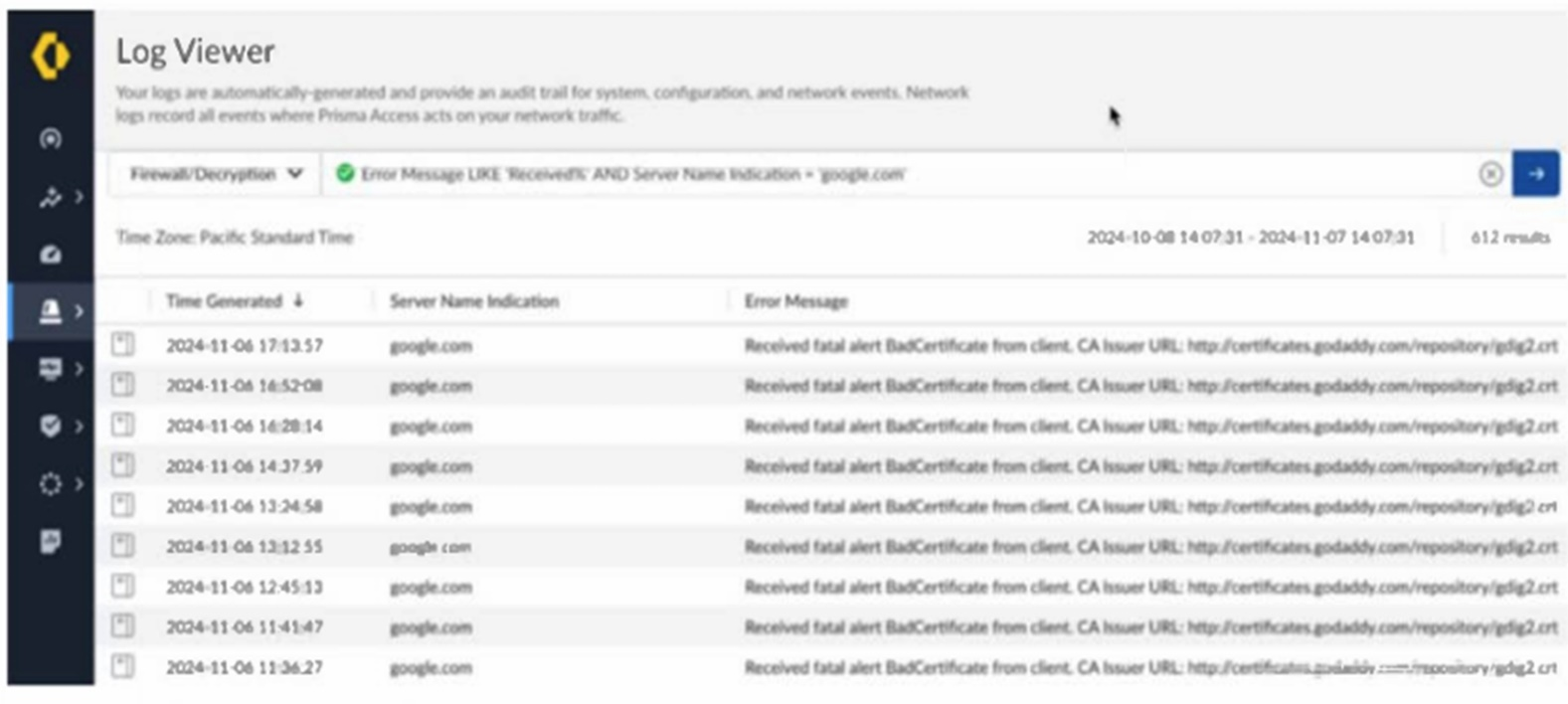
Answer : B, C
The error messages indicate that Prisma Access is encountering certificate issues while attempting to decrypt traffic to 'google.com.' This suggests that the server has pinned certificates, meaning it does not allow man-in-the-middle (MITM) decryption by Prisma Access. Since pinned certificates prevent traffic decryption, a solution is to create a 'do not decrypt' rule for the hostname 'google.com.' This will allow traffic to flow without triggering certificate errors while maintaining secure communication with Google's servers.
Which two configurations must be enabled to allow App Acceleration for SaaS applications? (Choose two.)
Answer : C, D
To enable App Acceleration for SaaS applications in Prisma Access, the following configurations must be enabled:
Trusted Root CA for the CA certificate ensures that Prisma Access can validate and trust the SaaS application's certificates, allowing seamless inspection and acceleration of traffic without security warnings.
Forward Trust Certificate for the CA certificate enables SSL decryption for SaaS applications, allowing Prisma Access to optimize traffic and apply acceleration techniques while maintaining security policies.
A malicious user is attempting to connect to a blocked website by crafting a packet using a fake SNI and the correct website in the HTTP host header.
Which option will prevent this form of attack?
Answer : D
This option ensures that SSL Decryption checks for mismatches between the Server Name Indication (SNI) field in the TLS handshake and the Common Name (CN) or Subject Alternative Name (SAN) in the server certificate. If a malicious user tries to bypass content filtering by spoofing the SNI while using the real blocked website in the HTTP host header, this setting will detect the discrepancy and block the session, preventing unauthorized access.
How can a senior engineer use Strata Cloud Manager (SCM) to ensure that junior engineers are able to create compliant policies while preventing the creation of policies that may result in security gaps?
Answer : A
By using security checks under posture settings in Strata Cloud Manager (SCM), the senior engineer can enforce policy compliance standards by automatically denying any security policy that does not align with best practices. This ensures that junior engineers can create policies while preventing configurations that might introduce security gaps. This proactive approach eliminates manual oversight and enforces compliance at the time of policy creation, reducing risk and ensuring consistent security enforcement.
An engineer configures a Security policy for traffic originating at branch locations in the Remote Networks configuration scope. After committing the configuration and reviewing the logs, the branch traffic is not matching the Security policy.
Which statement explains the branch traffic behavior?
Answer : D
In Prisma Access, security policies are evaluated based on their configuration scope. If the engineer configured a Security policy under the Remote Networks scope, but traffic from the branch locations is instead matching a Security policy under the Prisma Access configuration scope, the intended policy will not take effect. This happens because Prisma Access evaluates security rules based on the highest-level applicable configuration first, which can override more specific Remote Networks policies.
A customer using Prisma Access (Managed by Panorama) wants to monitor traffic patterns across all remote networks and use Strata Logging Service to gather insights on network usage. An engineer notices that some network data is missing from the Application Command Center (ACC).
What should the engineer do to ensure complete data visibility?
Answer : D
For complete data visibility in Prisma Access (Managed by Panorama), log forwarding profiles must be applied to all security policies to ensure that traffic logs are correctly sent to Strata Logging Service. If log forwarding is missing or misconfigured, some traffic data may not appear in the Application Command Center (ACC), leading to incomplete insights. Verifying and correctly assigning log forwarding ensures that all relevant network activity is captured and available for analysis.