Salesforce Implement and Manage CRM Analytics ANC-301 Exam Questions
Universal Containers uses CRM Analytics to build dashboards for different departments: Sales, Service, and Marketing. Users in the same department have the same role and need to have access to the same dashboards. Dashboards for different departments use some common datasets with the same row-level security.
How should a CRM Analytics consultant address this need?
Answer : C
For managing access to department-specific dashboards while leveraging common datasets, the best approach involves the use of apps and permission sets. Here's why:
App Segregation: Creating a separate app for each department (Sales, Service, Marketing) allows for tailored dashboards and datasets to be grouped by department, facilitating easier management and navigation.
Shared Common Datasets: Placing common datasets in a shared app ensures that all departments can access necessary data without duplication, maintaining consistency and reducing storage requirements.
Use of Permission Sets: Leveraging permission sets to control access to these apps is a flexible and scalable approach. Permission sets can be finely tuned to grant or restrict access based on user roles within the organization, and they can be easily adjusted as roles or organizational structures change.
This structure not only ensures data security and appropriate access but also enhances the efficiency of managing CRM Analytics resources across different departments.
Universal Containers wants to create two dashboards and has two user groups. The 'Regional Performance' dashboard should be accessible to sales reps and managers/executives to keep track of
how sales reps are performing in each region. Sales reps must only be able to see data pertaining to their respective region. The 'National Performance' dashboard is using the same data as the other
dashboard but should only be accessible to managers/executives to compare data across all regions.
In addition to row-level security to view only regional data, how should a consultant ensure that sales reps are unable to view the 'National Performance' dashboard?
Answer : A
A system administrator and a CRM Analytics consultant are working together on deploying arecipe/dataflow and a dataset to another org. Prior to this deployment, a package was deployed with all the custom fields used in the dataflow and dataset.
While running the recipe/dataflow in the target environment, the consultant encounters multiple errors related to these custom fields.
How should this be resolved?
Answer : B
Cloud Kicks (CK) wants to use CRM Analytics to analyze trends of its sales pipeline in order to accelerate the company's sales process. To do so, CK needs to know the average time an opportunity
spends in each stage. The data can be found in the Opportunity History object, but the value is not pre-calculated in Salesforce, so a consultant recommends using a recipe to calculate it.
How should the consultant use a recipe to calculate the average time an opportunity spends in each stage?
Answer : C
A manager at Cloud Kicks wants to separate and analyze accounts based on numeric information of its opportunity records. The data includes things like amount, quantity of products, contacts, and
quotes.
How should the CRM Analytics consultant accomplish this?
Answer : B
Universal Containers (UC) builds three Einstein Discovery models in Salesforce to predict and maximize its revenue per customer. The models are for every region UC has a business: EMEA, AMER, and APAC.
How should a consultant help UC deploy the three Einstein models to Salesforce?
Answer : B
In deploying Einstein Discovery models that are tailored to different regions (EMEA, AMER, and APAC), the best approach is to segment the account data by region and apply the specific model designed for each segment. This method ensures the following:
Relevance and Accuracy: Each model can be specialized to understand and predict based on regional dynamics, which may differ significantly across geographies in terms of market behavior, customer preferences, and economic conditions.
Efficiency: Deploying region-specific models avoids the dilution of predictive power that might occur if a single model were used across all regions, which could lead to less accurate predictions.
Scalability: This approach is scalable as UC can further refine each model as more regional data becomes available or as regional market conditions evolve.
Universal Containers has a well-defined role hierarchy in Salesforce where everyone is assigned to an appropriate node. The accounts within their instance are categorized by their demography.
An individual sales rep should be able to view all accounts that they own. In addition, sales reps should be able to see any accounts where the value of the account demography matches the demography defined on their user record. A user could have more than one demography defined on their user record.
To meet this requirement, the CRM Analytics consultant has set up a security predicate of the existing 'Account' dataset as follows:
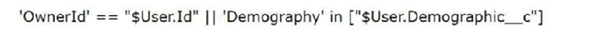
This, however, does not seem to be working as expected.
What is causing the issue?
Answer : A
The issue with the security predicate not functioning as expected likely stems from a permissions issue related to the custom field Demographic__c on the User object. Here's a detailed explanation:
Field-Level Security: If the sales reps do not have access to the Demographic__c field, the security predicate which references this field cannot execute properly as the system cannot evaluate the predicate without accessing the field.
Permission Settings: Ensuring that the sales reps have the necessary permissions to view and use the Demographic__c field is crucial for the security predicate to function correctly.
Data Visibility: The security model in CRM Analytics relies heavily on the underlying data permissions in Salesforce. If these permissions are not correctly configured, the expected data visibility through CRM Analytics will not be achieved.