Salesforce Certified MuleSoft Platform Architect (Mule-Arch-201) Exam Questions
Which layer in the API-led connectivity focuses on unlocking key systems, legacy systems, data sources etc and exposes the functionality?
Answer : C
Correct Answe r: System Layer
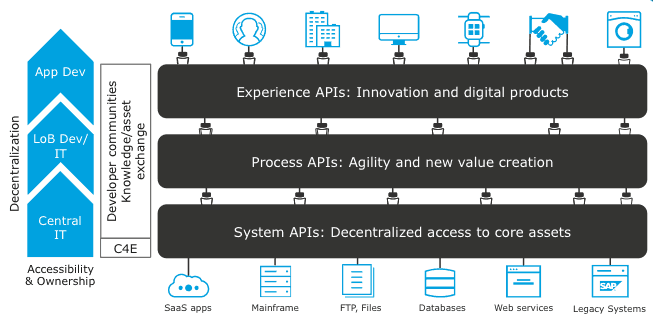
The APIs used in an API-led approach to connectivity fall into three categories:
System APIs -- these usually access the core systems of record and provide a means of insulating the user from the complexity or any changes to the underlying systems. Once built, many users, can access data without any need to learn the underlying systems and can reuse these APIs in multiple projects.
Process APIs -- These APIs interact with and shape data within a single system or across systems (breaking down data silos) and are created here without a dependence on the source systems from which that data originates, as well as the target channels through which that data is delivered.
Experience APIs -- Experience APIs are the means by which data can be reconfigured so that it is most easily consumed by its intended audience, all from a common data source, rather than setting up separate point-to-point integrations for each channel. An Experience API is usually created with API-first design principles where the API is designed for the specific user experience in mind.
An established communications company is beginning its API-led connectivity journey, The company has been using a successful Enterprise Data Model for many years. The company has identified a self-service account management app as the first effort for API-led, and it has identified the following APIs.
Experience layer: Mobile Account Management EAPI, Browser Account Management EAPI
Process layer: Customer Lookup PAPI, Service Lookup PAPI, Account Lookup PAPI
System layer: Customer SAPI, Account SAPI, Product SAPI, Service SAPI
According to MuleSoft's API-led connectivity approach, which API would not be served by the Enterprise Data Model?
Answer : C
In the API-led connectivity approach, APIs are categorized into Experience, Process, and System layers:
Enterprise Data Model Scope:
The Enterprise Data Model (EDM) generally supports System APIs and some Process APIs by defining standard data structures used across the organization. Experience APIs, however, are tailored to specific applications or interfaces and are less likely to be served directly by the EDM, as they may require customized data representations to meet the unique needs of each user interface.
Why Option C is Correct:
The Mobile Account Management EAPI serves mobile-specific needs and often requires data formatted differently from the standardized data models. Thus, it would be outside the direct scope of the EDM and might employ custom mappings to fit mobile application requirements.
of Incorrect Options:
Option A (Customer SAPI), Option B (Customer Lookup PAPI), and Option D (Service SAPI) would typically align with the EDM as they are closer to the core data and services the EDM supports.
Reference For additional guidance, review MuleSoft's best practices on API-led connectivity and data modeling.
A Mule application exposes an HTTPS endpoint and is deployed to the CloudHub Shared Worker Cloud. All traffic to that Mule application must stay inside the AWS VPC.
To what TCP port do API invocations to that Mule application need to be sent?
Answer : D
Correct Answe r: 8082
*****************************************
>> 8091 and 8092 ports are to be used when keeping your HTTP and HTTPS app private to the LOCAL VPC respectively.
>> Above TWO ports are not for Shared AWS VPC/ Shared Worker Cloud.
>> 8081 is to be used when exposing your HTTP endpoint app to the internet through Shared LB
>> 8082 is to be used when exposing your HTTPS endpoint app to the internet through Shared LB
So, API invocations should be sent to port 8082 when calling this HTTPS based app.
https://docs.mulesoft.com/runtime-manager/cloudhub-networking-guide
https://help.mulesoft.com/s/article/Configure-Cloudhub-Application-to-Send-a-HTTPS-Request-Directly-to-Another-Cloudhub-Application
How can the application of a rate limiting API policy be accurately reflected in the RAML definition of an API?
Answer : D
Correct Answe r:By refining the response definitions by adding thex-ratelimit-*response headers with description, type, and example
*****************************************
https://docs.mulesoft.com/api-manager/2.x/rate-limiting-and-throttling#response-headers
An organization has built an application network following the API-led connectivity approach recommended by MuleSoft. To protect the application network against
attacks from malicious external API clients, the organization plans to apply JSON Threat Protection policies.
To which API-led connectivity layer should the JSON Threat Protection policies most commonly be applied?
Answer : D
Understanding JSON Threat Protection Policies:
JSON Threat Protection policies are used to protect APIs from attacks that exploit JSON payloads, such as oversized payloads, deeply nested objects, and excessive array elements. This helps prevent Denial of Service (DoS) attacks and other malicious payload-related threats.
These policies are typically applied to safeguard APIs that are directly exposed to external clients, where the risk of receiving malicious payloads is highest.
API-led Connectivity Layers:
Experience Layer: This layer is designed to expose APIs to end-users or external API clients, often acting as the interface that interacts with users or applications.
Process Layer: This layer is used for orchestration and aggregation of data from various System APIs, typically operating within a trusted environment and not directly exposed to external clients.
System Layer: This layer provides access to backend systems and databases, often within the organization's secure environment and not directly accessible to external clients.
Evaluating the Options:
Option A (All layers): While JSON Threat Protection can technically be applied to all layers, it is most commonly applied at the Experience layer, where APIs are exposed to external traffic and are more vulnerable to attacks.
Option B (System layer): The System layer is generally not exposed to external clients directly, so JSON Threat Protection is less critical here.
Option C (Process layer): Similar to the System layer, the Process layer is typically internal and not exposed directly to external clients, so JSON Threat Protection is less commonly applied.
Option D (Correct Answer): The Experience layer is the correct answer because it is the layer that directly interacts with external clients, making it the primary target for malicious payloads. Applying JSON Threat Protection here effectively protects the application network from external threats.
Conclusion:
Option D is the correct answer, as the Experience layer is the most common layer for applying JSON Threat Protection policies to protect against external attacks.
For further reference, consult MuleSoft's documentation on API security policies and best practices for securing APIs at the Experience layer.
A company stores financial transaction data in two legacy systems. For each legacy system, a separate, dedicated System API (SAPI) exposes data for that legacy system. A Process API (PAPI) merges the data retrieved from ail of the System APIs into a common format. Several API clients call the PAPI through its public domain name.
The company now wants to expose a subset of financial data to a newly developed mobile application that uses a different Bounded Context Data Model. The company wants to follow MuleSoft's best practices for building out an effective application network.
Following MuleSoft's best practices, how can the company expose financial data needed by the mobile application in a way that minimizes the impact on the currently running API clients, API implementations, and support asset reuse?
Answer : A
To achieve the goal of exposing financial data to a new mobile application while following MuleSoft's best practices, the company should follow an API-led connectivity approach. This approach ensures minimal disruption to existing clients, maximizes reusability, and respects the separation of concerns across API layers.
of Solution:
Experience APIs for Client-Specific Requirements:
Create two new Experience APIs (EAPI-1 and EAPI-2) for the mobile application, tailored to meet the specific data and format requirements of the mobile application. These APIs encapsulate the client-specific needs and provide a custom interface without impacting other clients.
Process API Layer for Data Transformation:
By adding Mobile PAPI-2, we allow the mobile application to access the required subset of data, formatted according to the mobile application's requirements. This approach ensures that data transformation and aggregation are handled in the Process layer, maintaining consistency and reusability across different applications.
Reuse of System APIs:
Both the new Mobile PAPI-2 and existing PAPI-1 access data from System APIs (SAPI-1 and SAPI-2), which continue to expose data from each legacy system in a consistent, reusable manner. This avoids duplicating logic and ensures that data access remains centralized and manageable.
Why Option A is Correct:
Option A aligns with MuleSoft's best practices by isolating client-specific requirements in the Experience layer, utilizing Process APIs for data orchestration and transformation, and maintaining reusable System APIs for backend access.
This approach also ensures that the current API clients are not impacted, as new clients (e.g., the mobile app) interact with newly defined Experience APIs without modifying the existing API setup.
of Incorrect Options:
Option B: This option seems similar but lacks clarity on the separation of mobile-specific requirements and does not explicitly mention data transformation, which is essential in this scenario.
Option C: Creating a single mobile Experience API that exposes a subset of PAPI endpoints directly adds unnecessary complexity and may violate the separation of concerns, as transformation logic should not be in the Experience layer.
Option D: Deploying a new PAPI and using an API Proxy to redirect existing endpoints would add unnecessary complexity, disrupt the current API clients, and increase maintenance efforts.
Reference For additional guidance, refer to MuleSoft documentation on API-led connectivity best practices and best practices for structuring Experience, Process, and System APIs.
A developer from the Central IT team has created an initial version of the RAML definition in Design Center for an OAuth 2.0-protected System API and published it
to Exchange. Another developer from LoB IT discovered the System API in Exchange and would like to leverage it in the Process API.
What is the MuleSoft-recommended approach for Process API to invoke the System API?
Answer : C
In MuleSoft's ecosystem, when a Process API needs to consume a System API (published to Exchange and protected by OAuth 2.0), the recommended approach is to utilize the REST Connect Connector. Here's how it aligns with best practices:
Automated Connector Generation:
When a RAML or OAS specification is published in Exchange, MuleSoft automatically generates a REST Connect Connector for that API. This connector simplifies integration as it abstracts the complexity of making HTTP requests and handling OAuth authentication.
Streamlined Integration:
The Process API can import this generated connector from Exchange and configure OAuth credentials, streamlining secure access to the System API without manual HTTP setup.
Why Option C is Correct:
Using the REST Connect Connector directly leverages MuleSoft's automated tooling, minimizing manual configurations and ensuring a more maintainable integration.
of Incorrect Options:
Option A (importing an OAuth module) is unnecessary; OAuth is handled within the connector's configuration.
Option B (property YAML files with HTTP requests) involves manual setup, which is more error-prone and not recommended.
Option D (manually updating POM file) does not directly aid in invoking an API through Exchange.
Reference For more information on using REST Connect Connectors and OAuth integration in MuleSoft, refer to the MuleSoft documentation on API Management and Connectors.