VMware Associate VMware Security 1V0-81.20 Exam Questions
What are the four valid options for a Windows compliance rule based on firewall status in a Workspace ONE environment? (Choose four.)
Answer : A, C, D, E
Which network virtualization technologies can be used with an Ethernet VPN (EVPN) deployment in NSX-T Data Center? (Choose two.)
Answer : A, E
What types of hosts are supported for hosting both NSX-T Data Center managers and host transport nodes?
Answer : A
Refer to the exhibit.
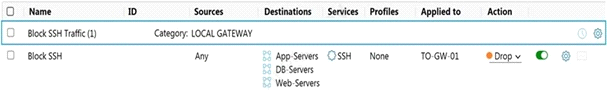
Which statement is true about the firewall rule?
Answer : A
Which four alert filters are available in the VMware Carbon Black Cloud Investigate page? (Choose four.)
Answer : A, B, C, F
Which shell command line syntax represents less suspicious danger than the others?
Answer : C
Which parameter ensures an endpoint will stay connected with the designated VMware Carbon Black Cloud tenant?
Answer : D