VMware 5V0-41.21 VMware NSX-T Data Center 3.1 Security Exam Practice Test
A security administrator has configured NSX Intelligence for discovery. They would like to get recommendations based on the changes in the scope of the input entities every hour.
What needs to be configured to achieve the requirement?
Answer : D
NSX Intelligence uses machine learning algorithms to analyze network traffic and provide recommendations for security and compliance. The administrator can configure the time range of the input entities to be analyzed, so that the recommendations are based on changes in the scope of the input entities over that period of time.
To achieve the requirement of getting recommendations based on the changes in the scope of the input entities every hour, the administrator needs to adjust the time range to 1 hour. This will ensure that the analysis and recommendations are based on the most recent hour of network traffic.
What is the NSX feature that allows a user to block ICMP between 192.168.1.100 and 192.168.1.101?
Answer : D
NSX Distributed Firewall is used to create firewall rules to control traffic between networks.
Refer to the exhibit.
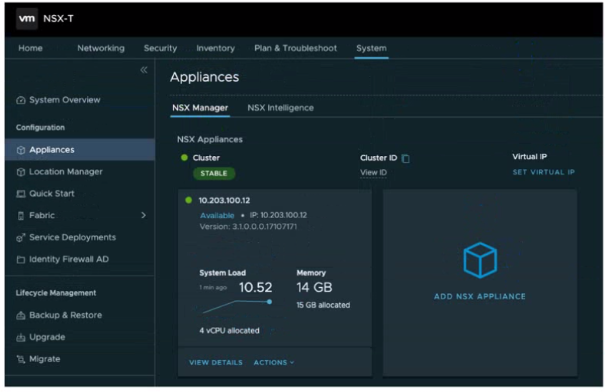
Referencing the exhibit, what is the VMware recommended number of NSX Manager Nodes to additionally deploy to form an NSX-T Manager Cluster?
Answer : B
Which two statements are true about NSX Intelligence? (Choose two.)
Answer : A, E
The two statements that are true about NSX Intelligence are that it assists to build service insertion with Partner SVM and that it supports planning of NSX-T Edge Firewall rules and policy. NSX Intelligence can be used in conjunction with vRealize Network Insight to provide visibility and insights into the network, but it cannot be used to visualize the physical infrastructure. Additionally, while it can help to plan firewall rules and policy, it does not support planning of distributed firewall rules and policy.
There has been a confirmed case of virus infection on multiple VMs managed by Endpoint Protection. A security administrator wants to create a group to quarantine infected VMs in the future.
What criteria will be used to build this group?
Answer : C
vSphere Tags are labels that can be used to group and categorize virtual machines and other objects. The security administrator can create a tag for quarantined VMs and assign it to any VMs that are confirmed to be infected. This will help identify and isolate the infected VMs more quickly and easily in the future.
Which is the port number used by transport nodes to export firewall statistics to NSX Manager?
Answer : B
The port number used by transport nodes to export firewall statistics to NSX Manager is 4789.